Welcome to the Psychological Change Laboratory!
Recommended
What is PsychLab?
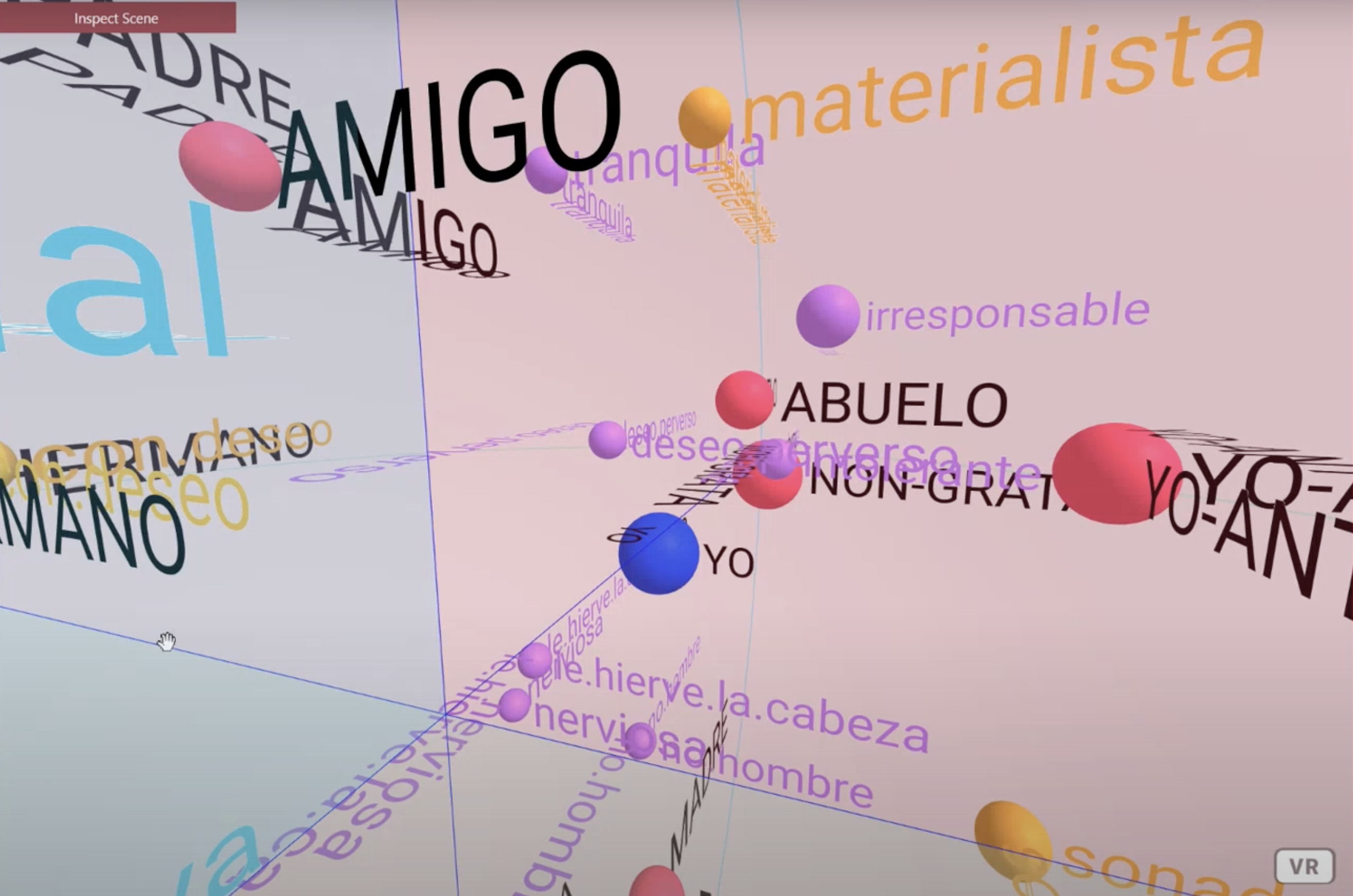
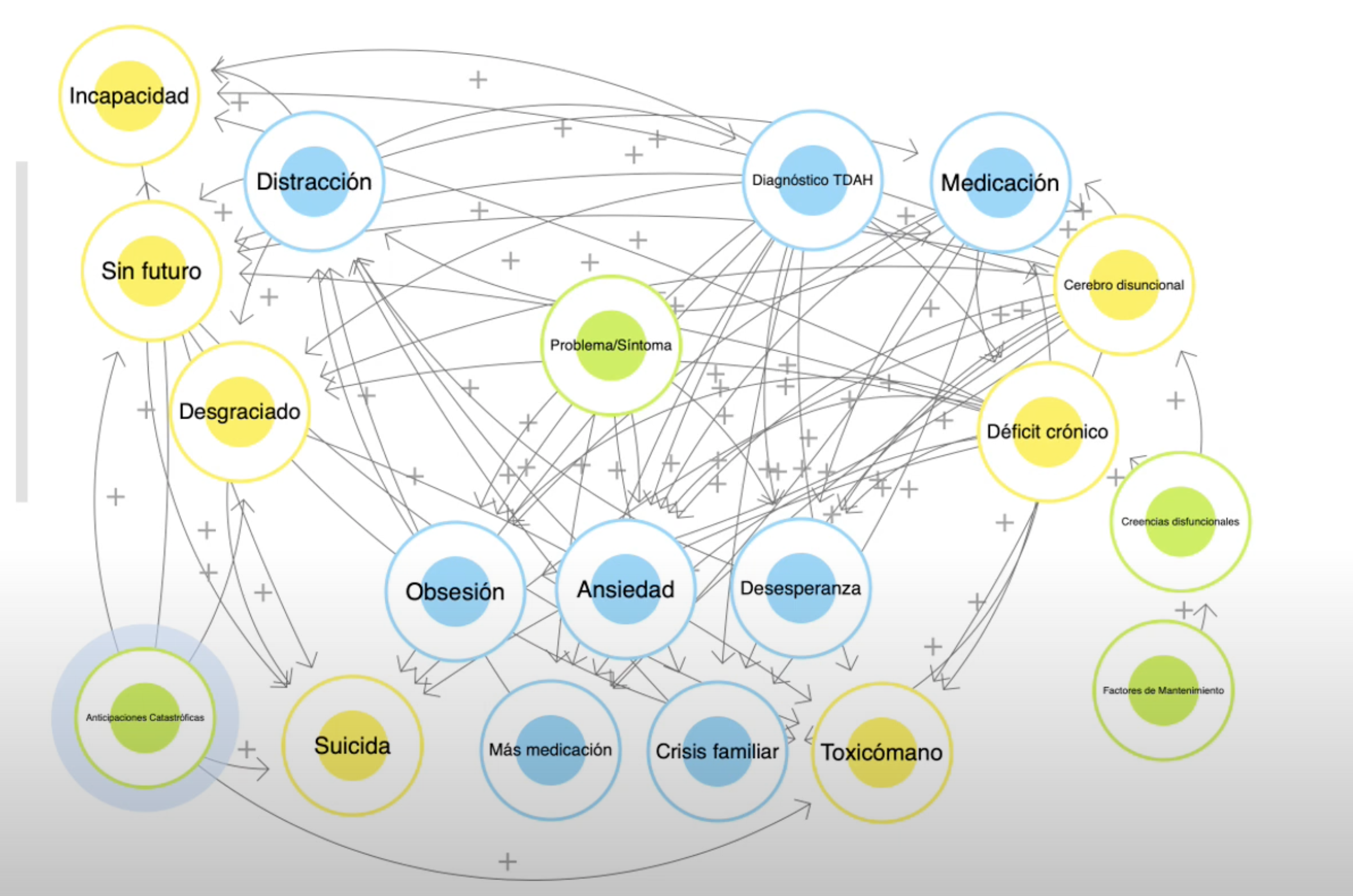
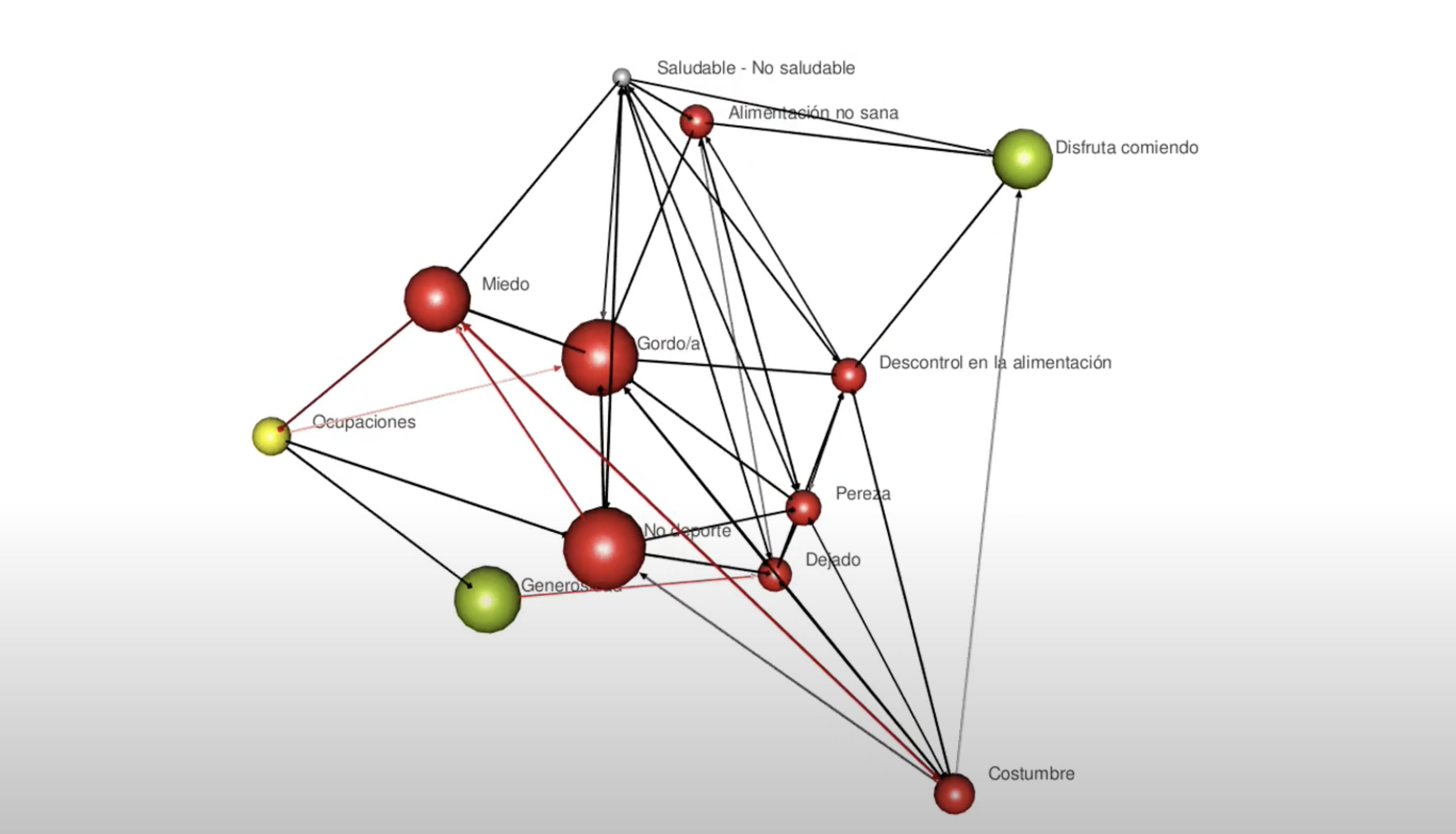
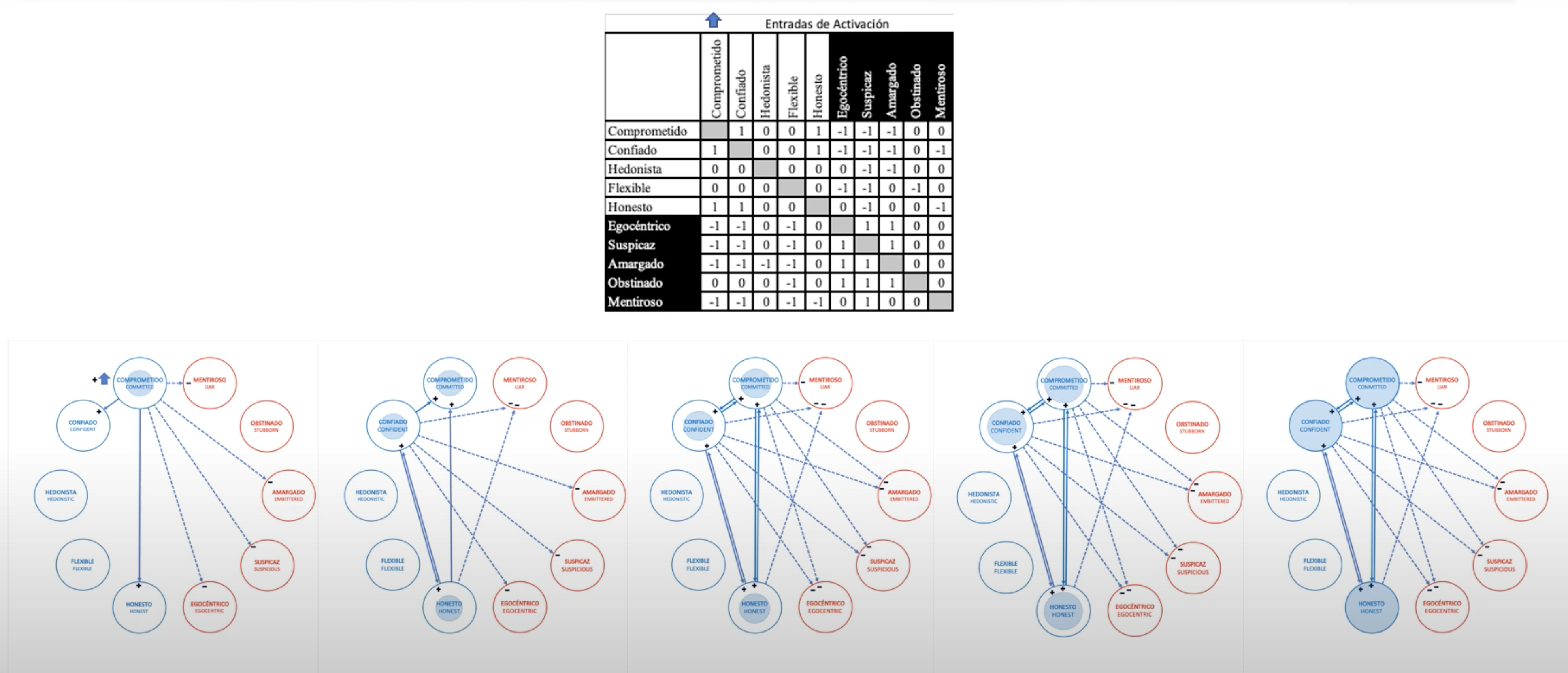
It is a virtual laboratory that contains tools for the exploration of the System of Personal Meanings, evaluation of its structure, representation of the system through Fuzzy Cognitive Maps and its dynamics of change through behavior vs. graphs. time that allow us to simulate the evolution of the System through mathematical modeling and identify psychological obstacles that hinder change.
What are the limitations of the free version of PsychLab?
With the free version of PsychLab, you can only add two tested subjects and one grid, and one implications grid for each of them.
How can I manage the subjects evaluated in PsychLab?
Once you are logged in to your account, you can manage your evaluated subjects by clicking on the “Patients” tab in the right navigation bar. Here you can add, edit, delete and observe all the people you have registered for evaluation
How can I generate a grid in PsychLab?
To generate a grid in PsychLab, you must select the patient you want to evaluate and add the grid. You can import a grid from an already filled out Excel template or create the grid through a form provided by PsychLab
What is the WimpGrid in PsychLab?
The WimpGrid is a semi-structured interview designed to explore how the person anticipates the consequences associated with changes in themselves.
To make a Fuzzy Cognitive Map, is it necessary to make a Grid?
It is not necessary to make a RepGrid. Through the laboratory, an MCB can be carried out directly by creating a wimpgrid.
Contact us
Send an email to psychlab@psi.uned.es and we will assist you as soon as possible.
Tutorials and Multimedia
Financing
Call for research grants 2022
Ignacio H. de Larramendi
Data Policy
- Content Protection
This website may collect data about you, use cookies, embed additional third-party tracking, and monitor your interaction with this embedded content, including tracking your interaction with the embedded content if you have an account and are logged in to this website. We collect data such as the visitor’s IP address and browser user agent string to help spam detection and organize activity logs.
If you are interested in publishing articles, links, comments or other content related to PsychLab, you can request it by writing to us at psychlab@psi.uned.es
- Registration and data protection
To ensure the security and privacy of our users’ data, we have taken a meticulous, multi-layered approach to our data protection policy. We are aware of the importance of security in today’s digital environment and, therefore, we have implemented various strategies and technologies, including the use of identity and access management platforms such as Keycloak, to reinforce our security measures.
We have established strict password policies to ensure our users choose strong, secure passwords. These policies include requirements on password length and complexity. Additionally, we conduct audits and maintain detailed records of user activities on our systems to effectively monitor and review security operations. This practice allows us to quickly identify and address any potential security vulnerabilities or incidents.
Compliance with ISO 27001
We comply with the ISO 27001 standard, an internationally recognized standard for information security management. This certification demonstrates our commitment to data protection and requires us to maintain a robust and continually improving Information Security Management System (ISMS). We follow the policies and procedures established in ISO 27001, which include risk identification and management, the implementation of effective security controls, and the continuous auditing of our processes.
Email Verification.
Email address verification is a crucial step in our registration and account management process. This practice ensures that important communications reach our users securely and provides a mechanism to regain account access if login credentials are lost.
Password protection..
At our organization, we understand the importance of protecting passwords effectively. That's why we use advanced hashing and salting techniques to ensure that all passwords stored on our system are difficult to crack, even in the unfortunate event of a data breach. This approach ensures that our users' sensitive information remains safe and secure.
Authentication and Authorization.
We have implemented a robust authentication and authorization system to manage access to our applications and services. Using Keycloak, we are able to offer a secure and convenient user experience by using Single Sign-On (SSO), allowing our users to access multiple services with a single set of credentials. This technology not only simplifies the login process for users, but also strengthens our security by minimizing the number of passwords they need to manage.
Two-Factor Security (2FA).
We recognize the importance of additional security, especially in critical operations. Therefore, we have implemented two-factor authentication (2FA) as a standard in our security policy. This measure requires users to provide a second form of verification, in addition to their password, to access their accounts, adding an additional layer of protection against unauthorized access.